Human Security Interaction in 2016
Current Graduate Students
Bharat Singh, Shashank Murthy, Suhas Chandrashekhar, Nikhil Kumar, Abhinav Mishra, Harish Malik, Arpit Mathur
Grounded Theory
Grounded Theory is an inductive Methodology. All research is based on data, or "Grounded on Data". Grounded Theory is a general method. It is the systematic generation of theory from systematic research. It is a set of rigorous research procedures leading to the emergence of conceptual categories. These concepts/categories are related to each other as a theoretical explanation of the action(s) that continually resolves the main concern of the participants in a substantive area. Grounded Theory can be used with either qualitative or quantitative data. [http://www.groundedtheory.com/what-is-gt.aspx]
Data Collection
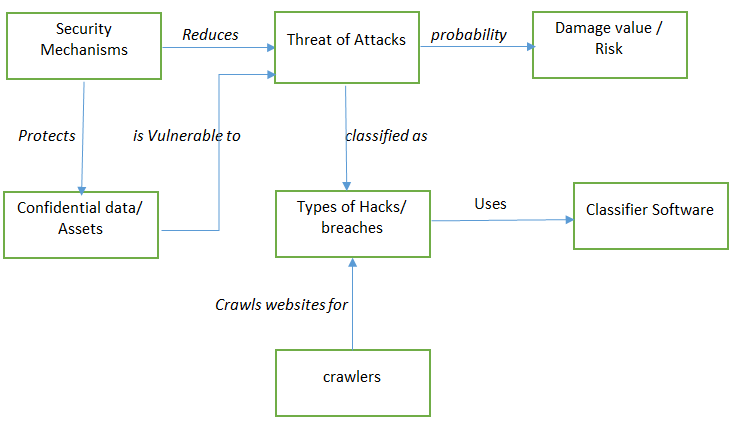
The progress in Data Collection Phase has been has taken the count of collected incidents by the team to around 18K. Data is collected using crawlers from various data sources. The Collected data spans various industries and a large domain of data breach incidents. The team made generated crawlers and scrappers for the websites. Crawlers: A computer program that browses the World Wide Web in order to scrape data from web pages. Scraper: A computer program that extracts data from a web page. This generally works using html tag structure to find the location of similar data around the page to extract them in an organized manner.
Taxonomy and Ontology
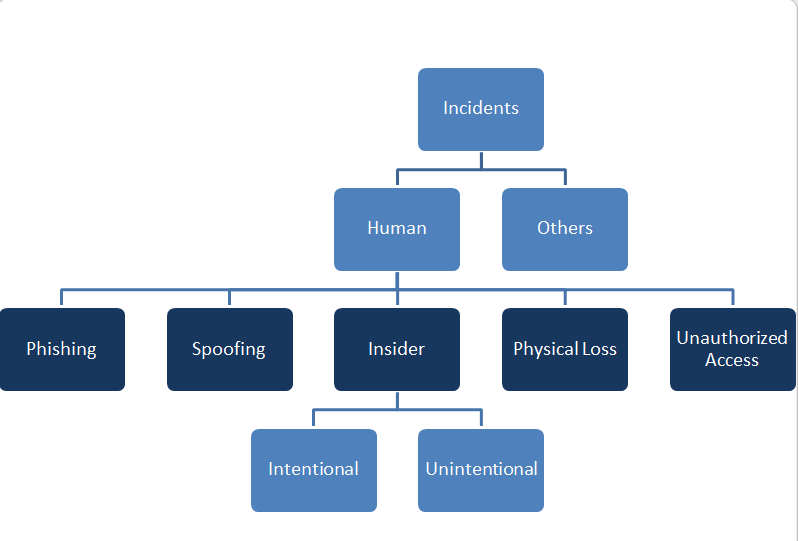
Cyber Security taxonomy is a classification of cyber security threats at various levels of detail. The main intent of this taxonomy is to establish a reference point for future threats encountered, while also providing a possibility to expand the current definitions and structure. In this regard, we consider this taxonomy to be a living structure that is being used and updated to maintain a consistent and detailed perspective on prevalent threats on the basis of collected information. An ontology is an explicit specification of a conceptualization. Data Braches Threat is high risk level, thus it is important to analyze its knowledge as ontology domain, share common understanding of the structure of information among people or software agents and enable reuse of domain knowledge.
 |
Taxonomy |
 |