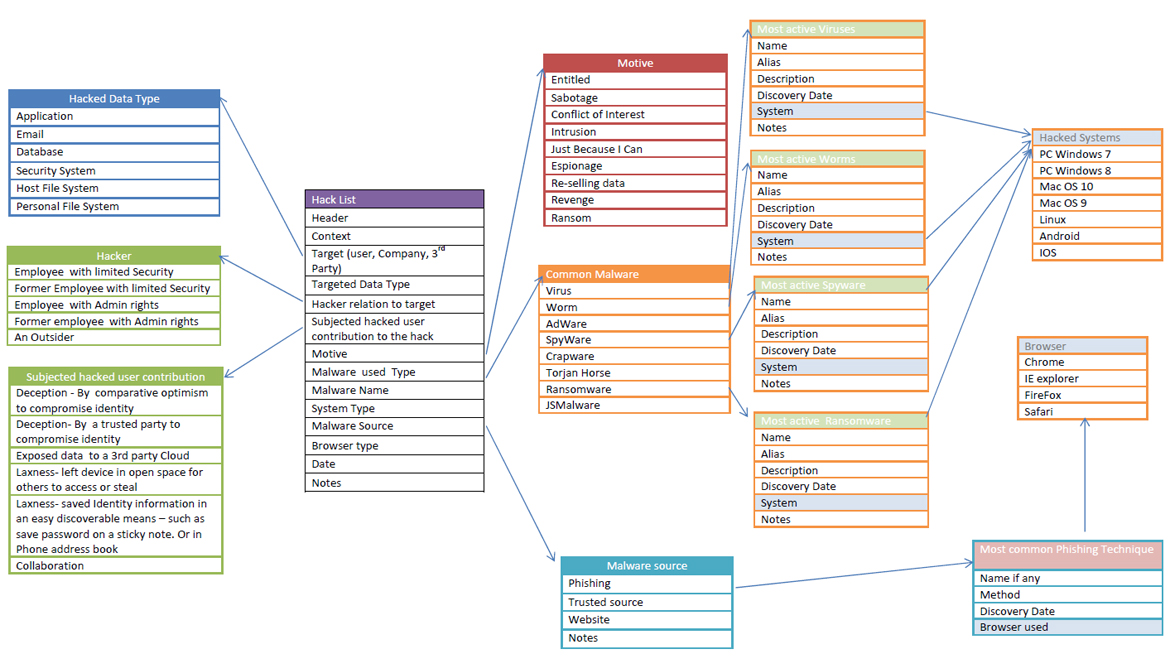
Model
Corporations and Host providers spend millions of dollars on building firewalls and data encryption to protect the data that are trusted with.
In many cases breaking through firewalls or trying to guess the encryption keys are very difficult if not impossible.
Hackers have much better luck preying on human weakness using deception and sometimes collaboration to gain access.
Hackers often use multi-tiered attacks. The first layer is often a phishinglayer to get the user to deploy a virus (Trojan horse)and/or get his credentials.
This is followed by data extraction, or in the case of Ransomware simply data encryption, with the hope that the user will pay a ransom to get their data back un-encrypted.
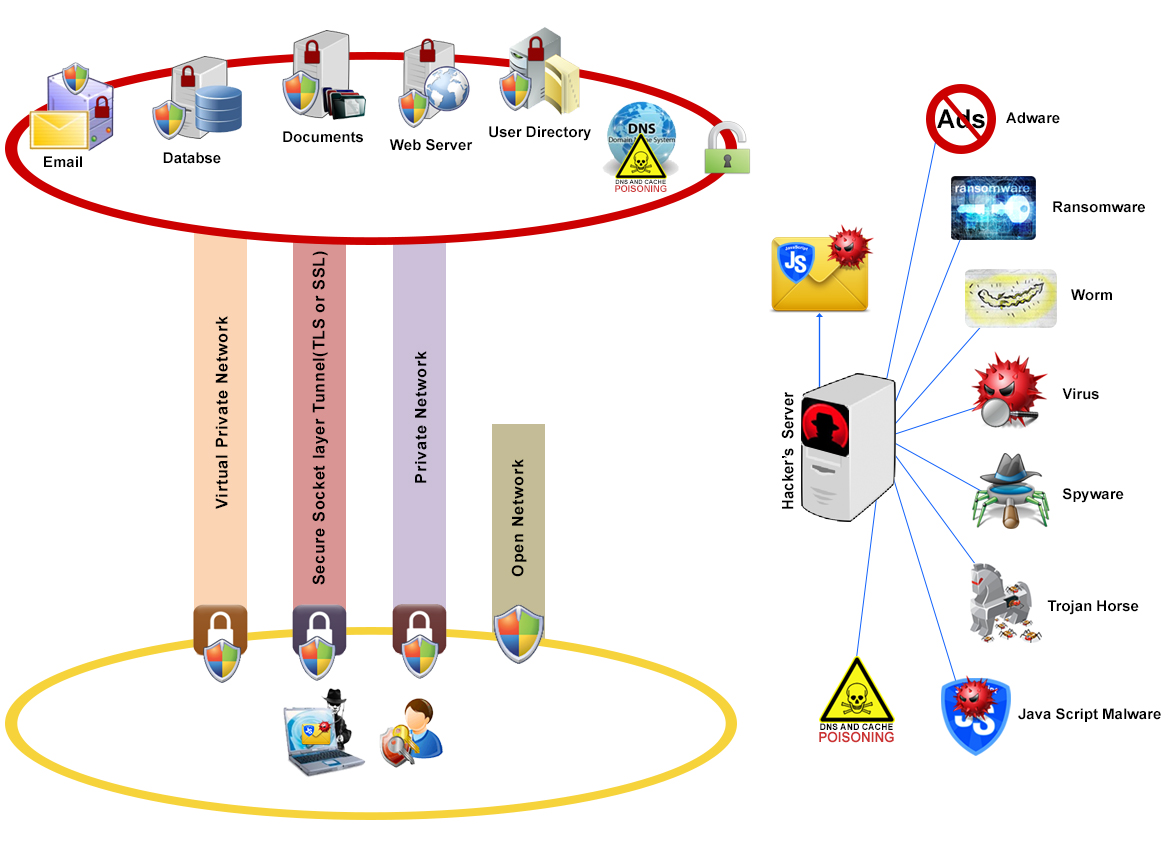
 Adware:
Adware: Adware is also known as advertising-supported software. It is software which renders advertisements for the purpose of generating revenue for its author.
The advertisements are published on the screen presented to the user at the time of installation. Adware is programmed to examine which Internet sites, the user visits frequently and to
present and feature related advertisements. Not all adware has malicious intent, but it becomes a problem anyway because it harms computer performance and can be annoying.
 Ransomware:
Ransomware: Ransomware is an advanced type of malware that restricts access to the computer system until the user pays a fee.
Your screen might show a pop-up warning that your have been locked out of your computer and that you can access only after paying the cybercriminal.
The cybercriminal demands a ransom to be paid in order for the restriction to be removed. The infamous Cryptolocker is one type of Ransomware.
 Worms:
Worms: A worm is similar to a virus by design and is considered to be a sub-class of a virus. Worms spread from computer to computer, but unlike a virus, it has the
capability to travel without any human action. A worm takes advantage of file or information transport features on your system, which is what allows it to travel unaided.
The biggest danger with a worm is its capability to replicate itself on your system, so rather than your computer sending out a single worm, it could send out hundreds or thousands
of copies of itself, creating a huge devastating effect. One example would be for a worm to send a copy of itself to everyone listed in your e-mail address book. Then, the worm replicates
and sends itself out to everyone listed in each of the receiver's address book, and the manifest continues on down the line. Due to the copying nature of a worm and its capability to travel
across networks the end result in most cases is that the worm consumes too much system memory (or network bandwidth), causing Web servers, network servers and individual computers to
stop responding. In recent worm attacks such as the much-talked-about Blaster Worm, the worm has been designed to tunnel into your system and allow malicious users to control your computer remotely.
 Virus:
Virus: A computer virus attaches itself to a program or file enabling it to spread from one computer to another, leaving infections as it travels. Like a human virus,
a computer virus can range in severity: some may cause only mildly annoying effects while others can damage your hardware, software or files. Almost all viruses are attached to an executable
file, which means the virus may exist on your computer but it actually cannot infect your computer unless you run or open the malicious program. It is important to note that a virus cannot be
spread without a human action, (such as running an infected program) to keep it going. Because a virus is spread by human action people will unknowingly continue the spread of a computer virus
by sharing infecting files or sending emails with viruses as attachments in the email.
 Spyware:
Spyware: This type of malicious software, spies on you, tracks your internet activities.
It helps the hacker in gathering information about the victim’s system, without the consent of the victim. This spyware’s presence is typically hidden from the host and it is
very difficult to detect. Some spyware like keyloggers may be installed intentionally in an organization to monitor activities of employees.
 Trojan:
Trojan: A Trojan Horse is full of as much trickery as the mythological Trojan Horse it was named after. The Trojan Horse, at first glance will appear
to be useful software but will actually do damage once installed or run on your computer. Those on the receiving end of a Trojan Horse are usually tricked into opening
them because they appear to be receiving legitimate software or files from a legitimate source. When a Trojan is activated on your computer, the results can vary.
Some Trojans are designed to be more annoying than malicious (like changing your desktop, adding silly active desktop icons) or they can cause serious damage by deleting
files and destroying information on your system. Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing
confidential or personal information to be compromised. Unlike viruses and worms, Trojans do not reproduce by infecting other files nor do they self-replicate.
 JSmalware:
JSmalware: Javascripts Malware are programs that run inside the browser. They are very commonly used with most websites to enhance user experience.
However hackers use them as a mechanism to phish user ID and password, deliver other Malware or render the browser un-usable.

The
Domain Name System (DNS) resolves domain names like yahoo.com, human can easily remember IP addresses needed for the purpose of computer services and
devices to interact. For example when a user wants to accessyahoo.com, the browser contacts the DNS to resolve yahoo.com DNS returns [206.190.36.45] for the IP address. All devices on a private
or public network are configured to use a particular DNS. For home user the default DNS is the router itself. Traditionally each corporation deploys internally its own local DNS.
DNS Poisoningis an attack, whereby the data is altered in local DNS. For example a hacker wants to re-route traffic from yahoo.com to his computer for Corporate XYZ. Attacker poison corporate XYZ
local DNS ,causing it to return his server IP address when resolving Yahoo.com.
 Hackers
Hackers’ most common ploy is to send an email, SMS, or even social media such as Facebook posting to their victims. The message contains attachments and or URL with a story that urges the user to access
the URL or download theattachments. Attachment and URL are embedded with Malwares. URLs are usually fake links to a commonly-known server to the user. As an example these links may appears to be pointing
to google,Paypal, dropbox etc... Closer look demonstrates that these links do not contain the proper domain name. The hacks with good success ratesare the ones where the hackers pose asa trusted source to
the victim,such asa co-worker, friend, or family member (most likely these people were hacked to be used as an accessory), where the likelihood to open the URL or attachments are much higher.
A sophisticated hack may poison the victim DNS to make the URL looks exactly like the original URL with proper domain name, while the URL really points to the hacker server. The user may use hacker’s server
unwittingly giving the hacker theultimate prize: the key to the data - the user credentials.All powersof firewalls and encryption that may or may not exist will fail to protect the data.
The problem is compounded when a user compromises a key that exposes data he is entrusted with which is not his own.

 Adware: Adware is also known as advertising-supported software. It is software which renders advertisements for the purpose of generating revenue for its author.
The advertisements are published on the screen presented to the user at the time of installation. Adware is programmed to examine which Internet sites, the user visits frequently and to
present and feature related advertisements. Not all adware has malicious intent, but it becomes a problem anyway because it harms computer performance and can be annoying.
Adware: Adware is also known as advertising-supported software. It is software which renders advertisements for the purpose of generating revenue for its author.
The advertisements are published on the screen presented to the user at the time of installation. Adware is programmed to examine which Internet sites, the user visits frequently and to
present and feature related advertisements. Not all adware has malicious intent, but it becomes a problem anyway because it harms computer performance and can be annoying.
 Ransomware: Ransomware is an advanced type of malware that restricts access to the computer system until the user pays a fee.
Your screen might show a pop-up warning that your have been locked out of your computer and that you can access only after paying the cybercriminal.
The cybercriminal demands a ransom to be paid in order for the restriction to be removed. The infamous Cryptolocker is one type of Ransomware.
Ransomware: Ransomware is an advanced type of malware that restricts access to the computer system until the user pays a fee.
Your screen might show a pop-up warning that your have been locked out of your computer and that you can access only after paying the cybercriminal.
The cybercriminal demands a ransom to be paid in order for the restriction to be removed. The infamous Cryptolocker is one type of Ransomware.
 Worms: A worm is similar to a virus by design and is considered to be a sub-class of a virus. Worms spread from computer to computer, but unlike a virus, it has the
capability to travel without any human action. A worm takes advantage of file or information transport features on your system, which is what allows it to travel unaided.
The biggest danger with a worm is its capability to replicate itself on your system, so rather than your computer sending out a single worm, it could send out hundreds or thousands
of copies of itself, creating a huge devastating effect. One example would be for a worm to send a copy of itself to everyone listed in your e-mail address book. Then, the worm replicates
and sends itself out to everyone listed in each of the receiver's address book, and the manifest continues on down the line. Due to the copying nature of a worm and its capability to travel
across networks the end result in most cases is that the worm consumes too much system memory (or network bandwidth), causing Web servers, network servers and individual computers to
stop responding. In recent worm attacks such as the much-talked-about Blaster Worm, the worm has been designed to tunnel into your system and allow malicious users to control your computer remotely.
Worms: A worm is similar to a virus by design and is considered to be a sub-class of a virus. Worms spread from computer to computer, but unlike a virus, it has the
capability to travel without any human action. A worm takes advantage of file or information transport features on your system, which is what allows it to travel unaided.
The biggest danger with a worm is its capability to replicate itself on your system, so rather than your computer sending out a single worm, it could send out hundreds or thousands
of copies of itself, creating a huge devastating effect. One example would be for a worm to send a copy of itself to everyone listed in your e-mail address book. Then, the worm replicates
and sends itself out to everyone listed in each of the receiver's address book, and the manifest continues on down the line. Due to the copying nature of a worm and its capability to travel
across networks the end result in most cases is that the worm consumes too much system memory (or network bandwidth), causing Web servers, network servers and individual computers to
stop responding. In recent worm attacks such as the much-talked-about Blaster Worm, the worm has been designed to tunnel into your system and allow malicious users to control your computer remotely.
 Virus: A computer virus attaches itself to a program or file enabling it to spread from one computer to another, leaving infections as it travels. Like a human virus,
a computer virus can range in severity: some may cause only mildly annoying effects while others can damage your hardware, software or files. Almost all viruses are attached to an executable
file, which means the virus may exist on your computer but it actually cannot infect your computer unless you run or open the malicious program. It is important to note that a virus cannot be
spread without a human action, (such as running an infected program) to keep it going. Because a virus is spread by human action people will unknowingly continue the spread of a computer virus
by sharing infecting files or sending emails with viruses as attachments in the email.
Virus: A computer virus attaches itself to a program or file enabling it to spread from one computer to another, leaving infections as it travels. Like a human virus,
a computer virus can range in severity: some may cause only mildly annoying effects while others can damage your hardware, software or files. Almost all viruses are attached to an executable
file, which means the virus may exist on your computer but it actually cannot infect your computer unless you run or open the malicious program. It is important to note that a virus cannot be
spread without a human action, (such as running an infected program) to keep it going. Because a virus is spread by human action people will unknowingly continue the spread of a computer virus
by sharing infecting files or sending emails with viruses as attachments in the email.
 Spyware: This type of malicious software, spies on you, tracks your internet activities.
It helps the hacker in gathering information about the victim’s system, without the consent of the victim. This spyware’s presence is typically hidden from the host and it is
very difficult to detect. Some spyware like keyloggers may be installed intentionally in an organization to monitor activities of employees.
Spyware: This type of malicious software, spies on you, tracks your internet activities.
It helps the hacker in gathering information about the victim’s system, without the consent of the victim. This spyware’s presence is typically hidden from the host and it is
very difficult to detect. Some spyware like keyloggers may be installed intentionally in an organization to monitor activities of employees.
 Trojan: A Trojan Horse is full of as much trickery as the mythological Trojan Horse it was named after. The Trojan Horse, at first glance will appear
to be useful software but will actually do damage once installed or run on your computer. Those on the receiving end of a Trojan Horse are usually tricked into opening
them because they appear to be receiving legitimate software or files from a legitimate source. When a Trojan is activated on your computer, the results can vary.
Some Trojans are designed to be more annoying than malicious (like changing your desktop, adding silly active desktop icons) or they can cause serious damage by deleting
files and destroying information on your system. Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing
confidential or personal information to be compromised. Unlike viruses and worms, Trojans do not reproduce by infecting other files nor do they self-replicate.
Trojan: A Trojan Horse is full of as much trickery as the mythological Trojan Horse it was named after. The Trojan Horse, at first glance will appear
to be useful software but will actually do damage once installed or run on your computer. Those on the receiving end of a Trojan Horse are usually tricked into opening
them because they appear to be receiving legitimate software or files from a legitimate source. When a Trojan is activated on your computer, the results can vary.
Some Trojans are designed to be more annoying than malicious (like changing your desktop, adding silly active desktop icons) or they can cause serious damage by deleting
files and destroying information on your system. Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing
confidential or personal information to be compromised. Unlike viruses and worms, Trojans do not reproduce by infecting other files nor do they self-replicate.
 JSmalware: Javascripts Malware are programs that run inside the browser. They are very commonly used with most websites to enhance user experience.
However hackers use them as a mechanism to phish user ID and password, deliver other Malware or render the browser un-usable.
JSmalware: Javascripts Malware are programs that run inside the browser. They are very commonly used with most websites to enhance user experience.
However hackers use them as a mechanism to phish user ID and password, deliver other Malware or render the browser un-usable.
 The Domain Name System (DNS) resolves domain names like yahoo.com, human can easily remember IP addresses needed for the purpose of computer services and
devices to interact. For example when a user wants to accessyahoo.com, the browser contacts the DNS to resolve yahoo.com DNS returns [206.190.36.45] for the IP address. All devices on a private
or public network are configured to use a particular DNS. For home user the default DNS is the router itself. Traditionally each corporation deploys internally its own local DNS.
DNS Poisoningis an attack, whereby the data is altered in local DNS. For example a hacker wants to re-route traffic from yahoo.com to his computer for Corporate XYZ. Attacker poison corporate XYZ
local DNS ,causing it to return his server IP address when resolving Yahoo.com.
The Domain Name System (DNS) resolves domain names like yahoo.com, human can easily remember IP addresses needed for the purpose of computer services and
devices to interact. For example when a user wants to accessyahoo.com, the browser contacts the DNS to resolve yahoo.com DNS returns [206.190.36.45] for the IP address. All devices on a private
or public network are configured to use a particular DNS. For home user the default DNS is the router itself. Traditionally each corporation deploys internally its own local DNS.
DNS Poisoningis an attack, whereby the data is altered in local DNS. For example a hacker wants to re-route traffic from yahoo.com to his computer for Corporate XYZ. Attacker poison corporate XYZ
local DNS ,causing it to return his server IP address when resolving Yahoo.com.
 Hackers’ most common ploy is to send an email, SMS, or even social media such as Facebook posting to their victims. The message contains attachments and or URL with a story that urges the user to access
the URL or download theattachments. Attachment and URL are embedded with Malwares. URLs are usually fake links to a commonly-known server to the user. As an example these links may appears to be pointing
to google,Paypal, dropbox etc... Closer look demonstrates that these links do not contain the proper domain name. The hacks with good success ratesare the ones where the hackers pose asa trusted source to
the victim,such asa co-worker, friend, or family member (most likely these people were hacked to be used as an accessory), where the likelihood to open the URL or attachments are much higher.
A sophisticated hack may poison the victim DNS to make the URL looks exactly like the original URL with proper domain name, while the URL really points to the hacker server. The user may use hacker’s server
unwittingly giving the hacker theultimate prize: the key to the data - the user credentials.All powersof firewalls and encryption that may or may not exist will fail to protect the data.
The problem is compounded when a user compromises a key that exposes data he is entrusted with which is not his own.
Hackers’ most common ploy is to send an email, SMS, or even social media such as Facebook posting to their victims. The message contains attachments and or URL with a story that urges the user to access
the URL or download theattachments. Attachment and URL are embedded with Malwares. URLs are usually fake links to a commonly-known server to the user. As an example these links may appears to be pointing
to google,Paypal, dropbox etc... Closer look demonstrates that these links do not contain the proper domain name. The hacks with good success ratesare the ones where the hackers pose asa trusted source to
the victim,such asa co-worker, friend, or family member (most likely these people were hacked to be used as an accessory), where the likelihood to open the URL or attachments are much higher.
A sophisticated hack may poison the victim DNS to make the URL looks exactly like the original URL with proper domain name, while the URL really points to the hacker server. The user may use hacker’s server
unwittingly giving the hacker theultimate prize: the key to the data - the user credentials.All powersof firewalls and encryption that may or may not exist will fail to protect the data.
The problem is compounded when a user compromises a key that exposes data he is entrusted with which is not his own.